|
 NETWORK
TUTORIAL NETWORK
TUTORIAL
Written by Robert Brian Brown This section discusses the various network components which make up a network. Its discusses cabling types, patch panels, connectors and network components like bridges, routers and ethernet switches. Brief Guide to BUILDING WIRING
A building wiring system covers a number of different elements Horizontal Wiring Some general features of the horizontal wiring
scheme are: Backbone
Wiring
Cabling
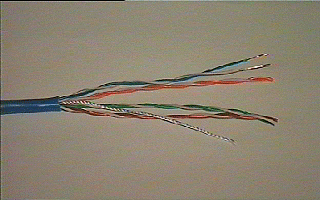
Types Unshielded Twisted Pair cable used in Category
5 looks like: Category 5 cable uses 8 wires. The length of
exposed wires is very critical, the standard limits this to less than 1/2"
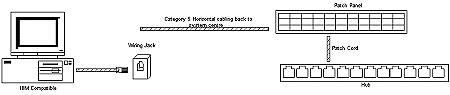
an inch. The various jack connectors look like: The patch cord which connects the workstation
to the wall jack looks like: In 10BaseT, each PC is wired back to a central hub using its own cable. There are limits imposed on the length of drop cable from the PC network card to the jack, the length of the horizontal wiring, and from the jack to the wiring closet.
This is obviously a physical STAR
configuration, in that each PC is wired back to a central point (the
Hub).
TWISTED PAIR ETHERNET HORIZONTAL WIRING (Solid 24Awg)
Each run < 80m from nearest hub Patch Cables Reversed cables are normally used for voice
systems. How to determine the type of patch
cable
If the colors are in the same order on both plugs, the cable is straight through. If the colors appear in the reverse order, the cable is reversed.
Coaxial Cable Thin coaxial cable [RJ-58AU], as used in
ethernet LAN's, looks like The connectors used in thin-net Ethernet LAN's
are T connectors (used to join cables together and attach to workstations)
and terminators (one at each end ofthe cable). The T-connectors and
terminators look like Fibre Optic Fibre optic is often used to overcome distance limitations. It can be used tojoin two hubs together, which normally could not be connected due to distancelimitations. In this instance, a UTP to Fibre convertor is necessary. Fibre obtic cable looks like In addition, fibre optic patch panels are used to interconnect fibre cables. These patch panels look like
NETWORK SEGMENTS
Large networks are made by combining several individual network segments together, using appropriate devices like routers and/or bridges.
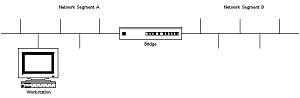
When network segments are combined into a single large network, paths exist between the individual network segments. These paths are called routes, and devices like routers and bridges keep tables which define how to get toa particular path. When a packet arrives, the router/bridge will look at thedestination address of the packet, and determine which network segment thepacket is to be transmitted on in order to get to its destination.
the above diagram, a packet arrives whose destination is segment B. The bridge forwards this incoming packet from segment A to the B segment.
SPANNING TREE ALOGRITHM
Sometimes, a loop would be created which caused the wrong packets to be sent on incorrect segments. These packets could loop around the network, being forwardedon, eventually arriving back, only to be forwarded on, etc. This quickly floodsthe network.The spanning tree algorithm is a software algorithm which defines how switchesand bridges can communicate and avoid network loops. Packets are exchanged between bridges/switches, and they establish a singlepath for reaching any particular network segment. This is a continous process,so that if a bridge/switch fails, the remaining devices can reconfigure therouting tables to allow each segment to be reached. To be effective, ensure that the bridges/switches in use in your network supportthis protocol.
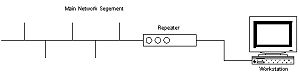
REPEATERS
Repeaters also allow isolation of segments in the event of failures or faultconditions. Disconnecting one side of a repeater effectively isolates theassociated segments from the network. Using repeaters simply allows you to extend your network distance limitations. It does not give you any more bandwidth or allow you to transmit data faster.
It should be noted that in the above diagram, the network number assigned tothe main network segment and the network number assigned to the other side of the repeater are the same. In addition, the traffic generated on one segment is propagated onto the other segment. This causes a rise in the total amount of traffic, so if the network segments are already heavily loaded, its not a good idea to use a repeater. Summary of features
BRIDGES During initialisation, the bridge learns about the network and the routes. Packets are passed onto other network segments based on the MAC layer. Each time the bridge is presented with a frame, the source address is stored. Thebridge builds up a table which identifies the segment to which the device islocated on. This internal table is then used to determine which segment incoming frames should be forwarded to. The size of this table is important, especially ifthe network has a large number of workstations/servers. The advantages of bridges are
The disadvantages of bridges are
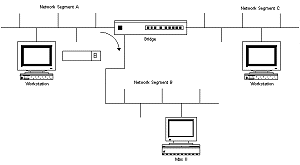
Transparent bridges (also known as spanning tree, IEEE 802.1 D) make all routing decisions. The bridge is said to be transparent (invisible) to the workstations. The bridge will automatically initialize itself and configure itsown routing information after it has been enabled. Bridges are ideally used in environments where there a number of well definedworkgroups, each operating more or less independant of each other, with occassional access to servers outside of their localised workgroup or network segment. Bridges do not offer performance improvements when used in diverse or scattered workgroups, where the majority of access occurs outside of the local segment. The diagram below shows two separate network segments connected via a bridge. Note that each segment must have a unique network address number in order for the bridge to be able to forward packets from one segment to the other.
Ideally, if workstations on network segment A needed access to a server, the best place to locate that server is on the same segment as the workstations, as this minimises traffic on the other segment, and avoids the delay incurred by the bridge. Summary of features
ROUTERS Routers were devised in order to separate networks logically. For instance, aTCP/IP router can segment the network based on IP subnets. Filtering at thislevel (on IP addresses) will take longer than that of a bridge or switch whichonly looks at the MAC layer. Most routers can also perform bridging functions. A major feature of routers, because they can filter packets at a protocol level, is to act as a firewall. This is essentially a barrier, which prevents unwanted packets either entering or leaving the network. Typically, and organisation which
connects to the Internet will install a router as the main gateway link
between their network and the outside world. Byconfiguring the router with
access lists (which define For example, an internal WWW server can be allowed IP access from external networks, but other company servers which contain sensitive data can be protected, so that external hosts outside the company are prevented access (you could even deny internal workstations access if required). Summary of features
HUBS In standard ethernet, all stations are connected to the same network segment inbus configuration. Traffic on the bus is controlled using the CSMA protocol, andall stations share the available bandwidth. Hubs dedicate the entire bandwidth to each port (workstation). Theworkstations attach to the hub using UTP. The hub provides a number of ports, which are logically combined using a single backplane, which often runs at amuch higher data rate than that of the ports. Ports can also be buffered, to allow packets to be held in case the hub or portis busy. And, because each workstation has their own port, they do not contendwith other workstations for access, having the entire bandwidth available fortheir exclusive use. The ports on a hub all appear as one single ethernet segment. In addition, hubs can be stacked or cascaded (using master/slave configurations) together, to add more ports per segment. As hubs do not count as repeaters, this is a better option for adding more workstations than the use of a repeater. Hub options also include an SNMP (Simple Network Management Protocol) agent. This allows the use of network management software to remotely administer and configure the hub. Detailed statistics related to port usage and bandwidth are often available, allowing informed decisions to be made concerning the state of the network. In summary, the advantages of hubs are,
ETHERNET SWITCHES When a packet arrives, the header is checked to determine which segment the packet is destined for, and then its forwarded to that segment.If the packet is destined for the same segment that it arrives on, thepacket is dropped and not retransmitted. This prevents the packet being"broadcasted" onto unnecessary segments, reducing the traffic. Nodes which inter-communicate frequently should be placed on the same segment. Switches work at the MAC layer level. Cut-Through Switches
Cross-bar switches Store-Forward
Switches
Other Forms of Ethernet
100 Megabit Ethernet Summary of features
Summary of features
In order to achieve the high 100Mbps rate, the collision timing associated with CSMA/CD is reduced. This means the total lengths of cabling from a workstation to another via two hubs cannot exceed 205 meters. If using fiber, a maximum distance of 405 meters from workstation to hub is allowed. 100BaseT devices are auto sensing, which means they can run at either speed. On startup, the card advertises their speed with a series of Fast Link Pulses. If a hub supports this, it will detect the FLP's, and then negotiate with the card for the highest possible speed. This can be over-ridden by network managers, who can force the slower 10Mbps mode. Summary of features
|